Why Mature IT Security Requires Analytics
Pressure is mounting on IT organizations to swiftly adapt to rapidly evolving security threats. You need to use every tool in your toolbox—especially analytics—to rise to these new challenges.
Too often, we think about analytics in the background. Yet, powerful, responsive analytics are as important as vulnerability scanners, automated testing, or workflow management tools.
Not only can trends and ad-hoc reports answer questions and provide information, but real-time operational dashboards can drive behavior to support secure processes.
Use Real-Time Dashboards to Drive Rapid Response to Security Incidents
The first step to rapid response is the ability for users to quickly prioritize and respond to issues as they arise.
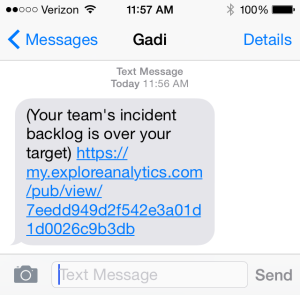
The following example is a quick report built with only a few clicks can show team members their work based on how long they’ve been open. This team leader’s report highlights security incidents that have been lingering for more than one day:
Logged-in users can drill through that report and act immediately. One global IT organization deployed aging reports and had a 30% reduction in stale incidents.
Here, analytics isn’t just a passive process of tracking success, it’s driving improved success.
Analyze Data On-The-Fly to Identify Security Threats
The ability to quickly build ad-hoc reports on-the-fly with a wealth of data is key to investigating issues. You need to have the capability to spot a problem, ask questions, get results, and propose solutions within just a few clicks.
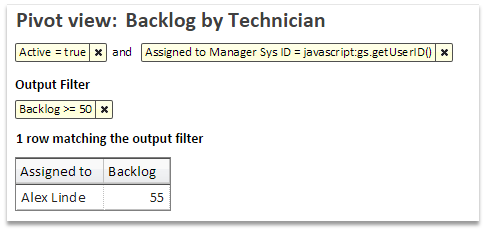
This next report harnesses the power of the CMDB to walk the relationships between CI’s and identify which business services are experiencing the most security incidents:
Looking at that report, it’s easily apparent that two of the most targeted services are both experiencing a lot of incidents related to their web servers.
Another example combines data from two different tables – Security Incident and Assets – to identify which models of assets are experiencing the most security incidents:
Now you are getting past the question of how many security incidents and into the answer of why. Are there specific models experiencing disproportionate issues? Could we improve security by phasing those models out?
Also, are you surprised to see in that example that “Unknown” asset model has the most security incidents? Probably not – that brings us to the last area where analytics drives improved security:
Leverage Analytics to Empower Users to Maintain Critical Reference Data
Data quality analytics bring together driving user behavior and investigating problems.
Data quality is the bedrock of processes because you can’t secure what you can’t see.
By creating a dashboard that shows data owners the quality of the data they’re responsible for, you can both drive improve compliance and resolve underlying issues proactively.
In the following dashboard, part of our pre-built CMDB Quality Application, has two components: KPIs showing the overall success of the data quality process, and a dashboard for owners of business services to see what data issues their services have:
Again, the dashboard transforms behavior, rather than assigning audit tasks on an annual basis that creates a lot of work all at once.
Analytics: The Bedrock of Ongoing Activity to Support Security
Are you using analytics as part of your security toolkit?
Analytics is a road to getting the entire organization working towards the same objectives, shaping their day-to-day activity towards quickly and thoroughly resolving issues with the information they need at their fingertips.